Mediatek devices PL Exploit(Preloader mode) (sec ctrl 0 status) peorocol is ready
As you know, in the new updates Mediatek devices do not allow access to bootrom in newer security
Generally only Preloader Mode is available, in new security updates we cannot switch the device from Preloader Mode to Brom Mode
We have written the protocol related to Preloader mode for various processors including MT68XX, which comes with the following features
This features no need to set TestPoint
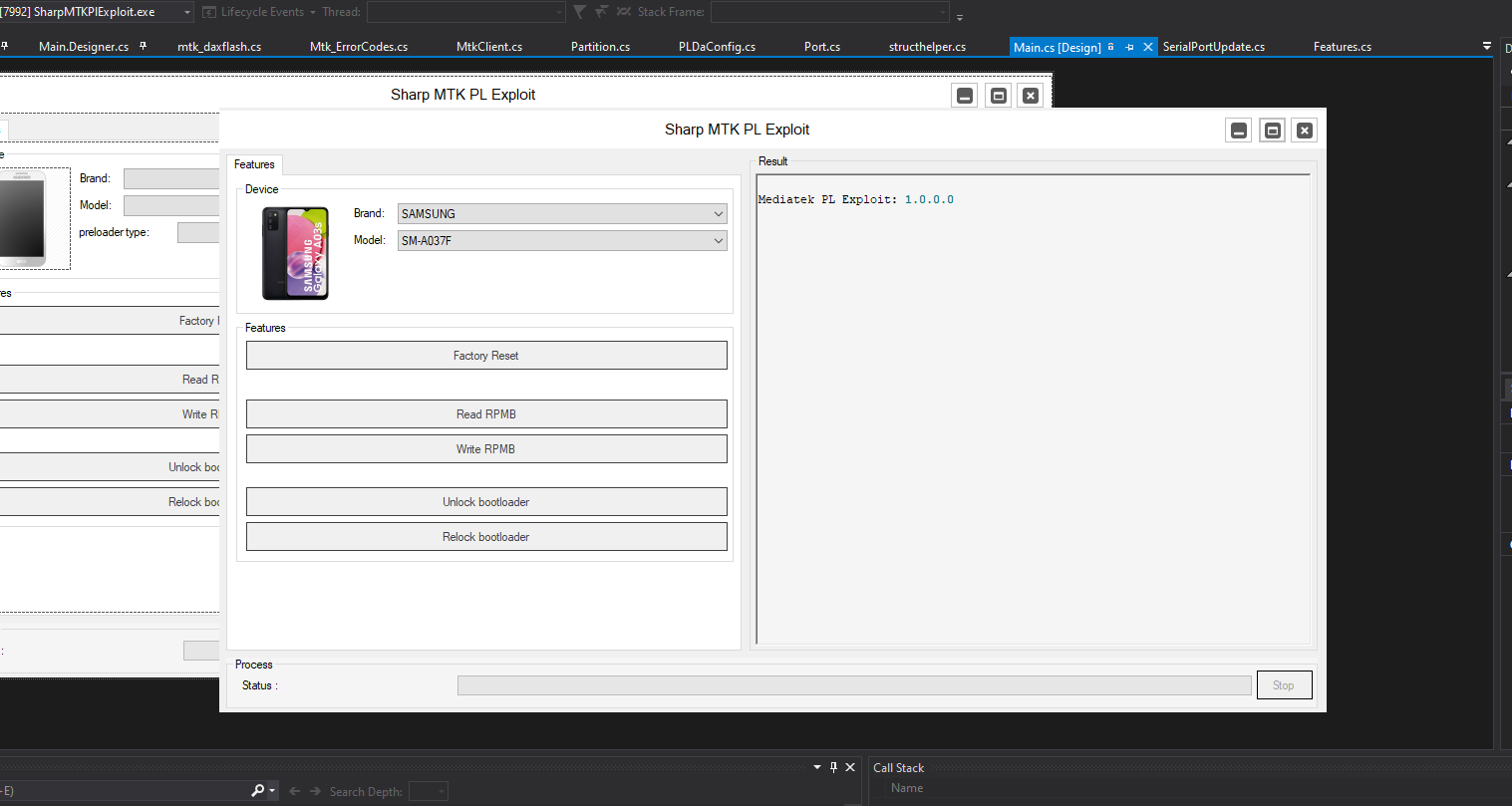
Features List:
- DA Parser
- bypass da1,da2 (+AES) and boot device DA
- Read GPT
- Parse GPT
- Read Partition (sector address)
- Write Partition (sector address)
- Erase Partition (sector address)
- Read RPMB
- Write RPMB
- Erase RPMB
- Unlock Bootloader
- Relock bootloader
- Factory Reset
- Execute CMDs
- ….
Supported Device :
- SAMSUNG
- OPPO
- VIVO
- TECHNO
Supported Platform List:
- MT67XX , MT68XX
- DA file is not ready for all MT67XX , MT68XX , but the devices we mentioned below in this post are ready for them. In the coming days, if new da files and code updates are applied, we will send them to you for free.
Tested On:
OPPO:
- Oppo A53 5G
- Oppo Reno4 SE
- Oppo A94 5G
- Oppo A95 5G
- Oppo F19 Pro+ 5G
- Oppo Reno5 Z
- Oppo Reno6 Z
- Oppo K7x
- Oppo A72 5G
SAMSUNG:
-
- SM-A037F
- SM-A042F
- SM-A045F
- SM-A226B
TECHNO, VIVO, OPPO, SAMSUNG with this CPU:
- MT6765
- MT6768
- MT6761
- MT6771
- MT6893
- MT6877
- MT6833
- MT6853
Source code is ready for:
C++\QT , C#.Net , VB.Net
Contact us: https://t.me/GsmCoder